GRC Analyst vs SOC Analyst: Everything You Need To Know
As technology advances, data breaches and cyberattacks are becoming increasingly common, organizations are investing heavily in cybersecurity measures. As a result, the demand for cybersecurity professionals has skyrocketed.
Among these are two prominent roles: GRC analyst vs soc analyst. While both positions play critical roles in protecting an organization’s information assets, they serve distinct purposes and require different skill sets.
This article discusses the intricacies of each role, exploring their definitions, responsibilities, salary expectations, certifications, job opportunities, and the industries they serve.
If you’re contemplating a career in cybersecurity but feel stuck choosing between these two roles, this article will walk you through the ins and outs of each position. By the end, you’ll have a clearer picture of which career path aligns with your skills, interests, and long-term goals.

RELATED: How to Become a GRC Analyst?
What is a GRC Analyst?
A Governance, Risk, and Compliance (GRC) Analyst, focuses on ensuring that an organization adheres to regulatory requirements and internal policies related to governance, risk management, and compliance. Their primary goal is to protect the organization from risks that can arise from regulatory non-compliance, operational inefficiencies, or reputational damage. Essentially, a GRC Analyst is the bridge between business operations and security regulations.
Key Responsibilities of a GRC Analyst:
- Acting as a subject-matter expert on relevant compliance and regulatory frameworks (E.g. HIPAA, ISO standards, PCI, SOC 2, GDPR, CCPA, etc), and staying on top of industry best practices.
- Engaging in risk management and updating playbooks to align with current industry standards, regulatory changes, and best practices
- Engaging in Disaster Recovery (DR) and Business Continuity Planning (BCP), and managing the testing of these plans
- Conducting compliance audits to ensure adherence to cybersecurity standards and regulations
- Monitoring compliance with regulations and standards, typically by key cybersecurity KPIs.
- Engaging in Third-Party Risk Management (TPRM) by analyzing and minimizing risks associated with outsourcing to third-party vendors or service providers.
- Assisting with documentation following incident response
- Security awareness and training
- Engaging in regulatory change management to make sure the companies policies and practices are adjusted following regulatory updates
- Preparing detailed reports and documentation of compliance findings and security gaps
- Developing and implementing controls to address cybersecurity and compliance needs across an organization.
- GRC Analysts typically collaborate with legal teams, senior management, and IT departments to create a cohesive strategy that minimizes risks and ensures compliance.
What is a SOC Analyst?
A Security Operations Center (SOC) Analyst is a frontline defender against cyberattacks. They work within a Security Operations Center to monitor, detect, and respond to cybersecurity threats in real-time. Their primary responsibility is to detect, analyze, and respond to cybersecurity threats and incidents.
What does a SOC analyst do?
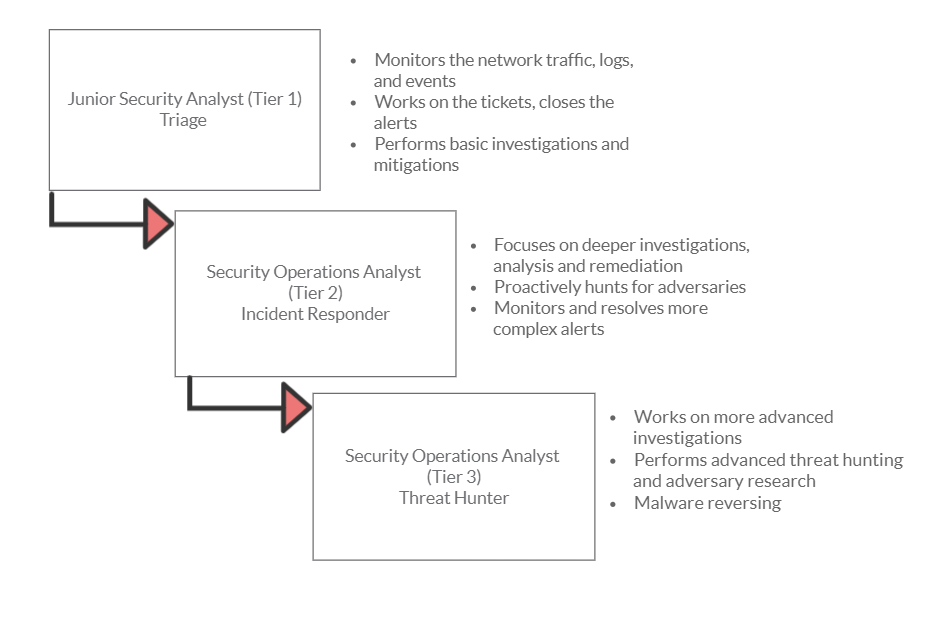
Some companies separate SOC analysts into three tiers. Here is a breakdown of each tier and what their roles look like.
- Tier 1—Triage: At this level, you will assess the severity and damage of security incidents and where they came from. Tier 1 SOC analysts provide the initial response to contain the threat and elevate matters that require more investigation and response to tier 2.
- Tier 2—Investigation and response: At the second level, you will provide further investigation for incidents referred to your team by the triage team, including where and how the incident occurred and the extent of the damage. Then, your team will conduct a complete response to the incident, including recovering data, creating reports, and recommending further action.
- Tier 3—Threat hunting and prevention: At the third level, you will seek out threats and look for insecurities in your network. Threat hunters are expert analysts who create detailed reports outlining areas for improvement, and they can sometimes detect sophisticated threats that bypass tier-1 security.
Key Responsibilities of a SOC Analyst:
- Monitoring security: An SOC analysts is responsible for continuous security monitoring for suspicious activity that could threaten security. This includes network traffic, software, all devices connected to the network, and cloud computing systems.
- Responding to incidents: When the SOC analysts discovers suspicious activity, they need to respond appropriately. SOC analysts will conduct a root cause investigation to determine the details of the incident and how it happened. Then they’ll work to limit the damage, such as by running antivirus software or removing access to compromised systems.
- Creating reports: SOC analysts are responsible for communicating when incidents occur and what events contributed to the security breach. SOC analysts may also create reports to demonstrate compliance with data privacy laws and regulations.
- Testing for vulnerabilities: Sometimes called threat hunting, SOC analysts conduct vulnerability testing on company systems, networks, and other resources to look for areas where security can be tightened and improved. Penetration testing is another form of vulnerability testing that simulates a cyberattack to test for organization preparedness.
- Implementing new security features: A SOC analyst ensures the organization has the most up-to-date security software and tools, including replacing outdated tools with newer technology.
- Regular maintenance: SOC analysts are responsible for maintaining the company’s assets, such as installing software patches, updating tools when needed, and reviewing security procedures.
- Asset recovery: After a threat has been eradicated, the SOC analysts must recover data and restore the assets. For example, a SOC analyst might need to restore a compromised device or processes that were shut down or isolated during recovery efforts.
- Post-mortem analysis: One way SOC analysts prevent cyberattacks from happening is by learning from their mistakes. A post-mortem analysis can help a SOC team understand what went wrong and develop new procedures and policies to prevent a similar attack.
ALSO READ: CompTIA Security Vs Google Cybersecurity Certification
Differences Between GRC Analysts and SOC Analysts
While both GRC Analysts and SOC Analysts are integral to an organization’s cybersecurity strategy, their focus and responsibilities differ significantly. Now that we’ve covered the basics, let’s dive deeper into how these roles differ across various dimensions.
Focus and Responsibilities
GRC Analyst
The focus of a GRC Analyst is governance, risk management, and compliance. They work on establishing policies, managing risks, and ensuring compliance with regulations. Their work is more strategic and involves long-term planning.
SOC Analyst
An SOC Analyst is primarily focused on operational security. They deal with real-time monitoring and response to security incidents. Their work is tactical, involving day-to-day operations to protect the organization from immediate threats.
Salary Expectations
Salary can vary significantly based on factors such as experience, location, and the size of the organization.
A GRC Analyst
According to Glassdoor, the average salary for a GRC Analyst in the United States. is around $85,000 per year, with entry-level roles starting at $60,000 and senior roles exceeding $110,000.
SOC Analyst
SOC Analysts earn an average of $75,000 per year, with entry-level salaries around $50,000 and senior positions reaching up to $105,000.
Why the Difference?
GRC roles often require a broader understanding of business operations and regulatory frameworks, which can command a higher premium. SOC Analysts, on the other hand, are technical specialists, and their salaries increase significantly as they gain experience and advanced certifications.
While SOC Analyst roles might offer faster entry points, GRC roles often provide higher earning potential as professionals climb the career ladder.
Certifications
Both GRC Analysts and SOC Analysts require specialized education and certifications to excel in their roles. Certifications can significantly enhance career prospects and earning potential in both roles. Here are some common certifications and educational requirements for each role:
GRC Analyst Certifications:
- Certified Information Systems Auditor (CISA): Focuses on auditing, control, and assurance.
- Certified in Risk and Information Systems Control (CRISC): Concentrates on risk management.
- Certified Information Systems Security Professional (CISSP): A broad certification covering various aspects of information security.
- Certified in Governance of Enterprise IT (CGEIT): Focuses on governance principles.
SOC Analyst Certifications:
- Certified Information Systems Security Professional (CISSP): Also relevant for SOC Analysts due to its comprehensive coverage of security principles.
- CompTIA Security+: An entry-level certification that covers foundational security concepts.
- Certified Ethical Hacker (CEH): Focuses on penetration testing and ethical hacking techniques.
- GIAC Security Essentials (GSEC): Covers a wide range of security topics relevant to SOC operations.
While GRC certifications emphasize governance and compliance, SOC certifications focus on technical skills and incident response capabilities.
MORE ARTICLES LIKE THIS: GRC Analyst Interview Questions
Job Opportunities and Career Path

The demand for both GRC Analysts and SOC Analysts is high and growing rapidly. According to the Bureau of Labor Statistics, employment of information security analysts, including SOC Analysts, is projected to grow 31% from 2020 to 2030, much faster than the average for all occupations.
Similarly, the demand for GRC Analysts is driven by the increasing need for organizations to comply with regulatory requirements and manage risk. According to a report by MarketsandMarkets, the global GRC market is expected to grow from $24.7 billion in 2020 to $47.4 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 13.6%.
Both roles offer promising career paths, but they lead to different opportunities.
GRC Analyst Career Path:
Entry-level positions may include roles such as Risk Analyst or Compliance Specialist.
With experience, professionals can advance to positions like GRC Manager, Risk Manager, or Chief Compliance Officer (CCO).
GRC Analyst: Can progress to roles like CISO, GRC Manager, or Risk Management Consultant.
GRC roles are particularly in demand in industries heavily regulated by laws and standards, such as:
- Finance (banks, insurance companies)
- Healthcare (hospitals, biotech firms)
- Critical Infrastructure (energy, utilities)
- Government (public sector compliance)
According to LinkedIn, GRC roles have grown by 24% in the last two years, with increased emphasis on compliance due to evolving privacy laws like GDPR and CCPA.
SOC Analyst Career Path:
Entry-level positions often include roles like Security Analyst or Incident Response Analyst.
Experienced SOC Analysts can move up to positions such as SOC Manager, Threat Intelligence Analyst, or Cybersecurity Architect.
SOC roles are crucial in industries with high cybersecurity threats, such as:
- Technology and Software
- Telecommunications
- Defense and Military
- Retail and E-commerce (compliance with PCI-DSS)
A study by Cybersecurity Ventures estimates that SOC roles will grow by 33% by 2025, driven by the rising frequency and sophistication of cyberattacks.
SOC Analyst: Can advance to positions like Security Analyst, Threat Intelligence Analyst, or Security Engineer.
READ ALSO: Cybersecurity Salary: A Comprehensive Guide
Industries of Employment
Both GRC Analysts and SOC Analysts can find employment across various industries, but some sectors may have a higher demand for one role over the other.
GRC Analysts:
Commonly found in heavily regulated industries such as finance, healthcare, government, energy and utilities.
Organizations in these sectors require strict compliance with regulations and standards, making GRC Analysts vital to their operations.
SOC Analysts:
SOC Analysts are in demand across a broader range of industries, due to the universal need for cybersecurity. Common industries include: Technology and IT services, Defense and aerospace, E-commerce and retail, and Telecommunications.
Any organization that relies on digital infrastructure and data processing requires SOC Analysts to manage and respond to security threats.
Skills Required
The skill sets for GRC Analysts and SOC Analysts differ significantly, reflecting their distinct roles.
GRC Core Analyst Skills:
Developing certain skills is essential for excelling as a GRC analyst:
- Analytical Thinking: GRC analysts need to assess complex situations, identify risks, and devise strategic solutions.
- Attention to Detail: Precise attention to regulations, policies, and potential risks is vital to ensure compliance and mitigate vulnerabilities.
- Communication: Effective communication is key to conveying GRC concepts, policies, and issues to various stakeholders, including non-technical audiences.
- Problem-Solving: GRC analysts need to tackle compliance challenges, resolve issues, and make informed decisions.
- Research Skills: Keeping up-to-date with evolving regulations and industry best practices requires strong research capabilities.
SOC Analyst Skills
To become a SOC analyst, you will need to develop a base of cybersecurity and technology skills, as well as build abilities for working in a team. To succeed in this role, it’s important to have key technical and workplace skills.
Technical skills represent the practical aspects of your role, while workplace skills contribute to how productive you are in a work environment. Below are some skills you’ll need:
Technical skills
- Endpoint analysis
- Operating systems
- Vulnerability recognition
- Familiarity with the hacker lifecycle
- Coding and database languages
- Network defense
- Incident response
- Computer forensics
Workplace skills
- Analytical skills
- Critical thinking
- Teamwork
- Communication
What tools do GRC analysts use?

1. RSA Archer: RSA Archer is a widely recognized and highly regarded GRC tool that provides a framework for organizations to proactively manage governance, risk, and compliance while enhancing overall security and resilience. It offers various modules to address diverse GRC needs.
Features:
- Risk management and assessment
- Incident and issue management
- Audit management
- Policy and procedure management
- Automated tasks to increase efficiency
- Third-party risk management
- Streamlined compliance tracking and reporting
- Highly customizable to adapt to specific business needs
2. Hyperproof: Hyperproof is a cloud-based GRC platform that provides streamlined compliance management through automated tracking, customized workflows, and collaboration tools, enhancing organizations’ governance and risk management practices.
Features:
- Automated workflows for audit and compliance tasks
- User-friendly interface
- Real-time monitoring of compliance status
- Centralizes documentation and evidence for audits
3. Riskonnect: Riskonnect provides a holistic approach to GRC by seamlessly integrating risk management, compliance, and internal audit functions. It delivers a unified solution that enables businesses to recognize, evaluate, and mitigate risks while ensuring regulatory compliance.
Features:
- Unified risk management platform
- Real-time risk assessment
- Incident tracking and analysis
- Compliance reporting and monitoring
4. ServiceNow: ServiceNow offers extensive GRC functionality by expanding its capabilities beyond IT service management. Its integrated approach unifies GRC processes, enabling organizations to seamlessly identify, handle, and address risks.
Features:
- Automated risk identification
- Compliance policy enforcement
- Continuous monitoring
- Audit trail and reporting
5. StandardFusion: StandardFusion focuses on simplifying compliance management through automation and a user-friendly interface. It helps businesses map controls to different regulations, ensuring alignment and providing a clear overview of compliance status.
Features:
- Policy and control management
- Risk assessment and mitigation
- Vendor risk management
- Audit preparation and reporting
6. IBM OpenPages: IBM OpenPages provides a risk and compliance management platform that helps organizations identify, assess, and monitor risks effectively. It provides a comprehensive view of an organization’s risk landscape, enabling users to make informed decisions confidently.
Features:
- Control testing and assessment
- Regulatory compliance tracking
- Issue and action management
- Advanced reporting and analytics
7. ZenGRC: ZenGRC is a cloud-based GRC tool designed to simplify the complexities of GRC processes. It facilitates collaboration, streamlines operations, and provides a centralized repository for tracking risks, compliance activities, and audits.
Features:
- User-friendly GRC software
- Risk assessment and tracking
- Task management and collaboration
- Real-time compliance monitoring
9. Enablon GRC: Enablon GRC platform helps organizations manage environmental, health, safety, and sustainability risks and compliance. It enables data-driven decision-making to improve organizational performance.
Features:
- Risk assessment and analysis
- Incident management
- Audit trail and reporting
- Compliance dashboards
10. Fusion Framework System: Fusion Framework System is a holistic GRC platform focusing on risk management and business continuity. It helps organizations develop resilient strategies by identifying potential disruptions and creating actionable plans.
Features:
- Business impact analysis
- Incident response planning
- Compliance management
- Comprehensive risk assessment
What tools do SOC analysts use?

Security operations center analysts use many tools to complete their work, including:
- Asset discovery: This software helps you manage your devices and configurations. Asset discovery can also help you mitigate risks and diagnose problems.
- Vulnerability assessment: This software scans your entire network for vulnerabilities to help prevent incidents before they occur.
- Intrusion detection: This tool monitors traffic passing through your network to look for threats and suspicious behavior.
- Endpoint detection: Endpoint detection monitors potential threats on endpoints, which are user devices like laptops and smartphones.
- User entity and behavior analytics: This software helps monitor for threats by analyzing user behavior for suspicious activity that doesn’t adhere to normal use.
- Security information and event management (SIEM): SIEM platforms combine tools to help SOC analysts automate threat detection efforts and streamline security operations.
SEE OTHERS: Can You Get a Job with Google Cybersecurity Certificate? Find Out How
Which Role is Right for You?
Both GRC and SOC Analyst roles are integral to cybersecurity, but they cater to different career aspirations.
The decision to pursue a career as a GRC or SOC Analyst depends on individual interests and strengths. If you enjoy strategic thinking, risk management, and compliance, a GRC role might be a good fit. If you are passionate about technical security, threat detection, and incident response, a SOC role could be more appealing.
Choose GRC If You:
- Enjoy policy-making and regulatory compliance.
- Prefer a broader view of organizational risk.
- Want to work closely with business leaders and stakeholders.
Choose SOC If You:
- Thrive in fast-paced, high-pressure environments.
- Have a passion for technical problem-solving and incident response.
- Want to stay on the cutting edge of cybersecurity technology.
Pros and Cons
GRC Analyst
Pros:
- Higher average salary potential.
- Opportunities to influence organizational strategy.
- Lower burnout risk compared to SOC roles.
Cons:
- Slower entry into the field.
- Requires a deep understanding of complex regulations.
SOC Analyst
Pros:
- Easier entry-level access.
- Opportunities for hands-on technical experience.
- High demand across industries.
Cons:
- High-stress environment.
- Potential for burnout due to 24/7 operations.
Challenges as a GRC Analyst
Being a Governance, Risk, and Compliance (GRC) analyst comes with a range of challenges due to the complex and dynamic nature of the role. Here are some of the challenges you might face.
- Regulatory Complexity:
Keeping up with the ever-changing landscape of regulations and compliance standards can be daunting. Different industries and regions have their own unique sets of regulations, and staying updated with them requires continuous learning and adaptation. - Data Management:
GRC analysts deal with a significant amount of data, including compliance requirements, risk assessments, and governance policies. Managing, organizing, and analyzing this data effectively can be challenging, especially as organizations grow and the volume of data increases. - Integration of GRC Processes:
Integrating GRC processes across different departments and systems can be difficult. Many organizations have disparate systems for managing different aspects of GRC, and making them work seamlessly together requires coordination and technical expertise. - Cultural Resistance:
Implementing and enforcing compliance and risk management practices might face resistance from employees and departments that perceive these measures as bureaucratic or hindrances to their operations. Overcoming this resistance and fostering a culture of compliance can be a challenge. - Risk Assessment Accuracy:
Conducting accurate risk assessments requires a deep understanding of the business, industry, and potential threats. GRC analysts need to balance qualitative and quantitative data to assess risks effectively and prioritize them appropriately. - Emerging Risks:
New risks can emerge rapidly due to technological advancements, industry shifts, or global events. Anticipating and addressing these emerging risks effectively requires the ability to think ahead and adapt quickly. - Communication and Collaboration:
GRC analysts often need to communicate complex regulatory and risk-related information to stakeholders across various levels of the organization. Effective communication and collaboration skills are crucial to ensure everyone understands the importance of GRC efforts. - Resource Constraints:
GRC efforts require resources, including time, personnel, and technology. Limited resources can hinder the implementation of robust GRC programs and make it challenging to cover all necessary areas adequately. - Audits and Assessments:
GRC analysts are often responsible for preparing the organization for audits and assessments by regulatory bodies or third parties. Ensuring that all necessary documentation and processes are in place for a successful audit can be demanding.
Overcoming these challenges requires a combination of technical knowledge, strong interpersonal skills, adaptability, and a commitment to ongoing learning. GRC analysts play a critical role in helping organizations operate ethically, securely, and in compliance with regulations, making their efforts essential despite the challenges they face.
Challenges as an SOC Analyst
- Too Many Alerts
On average, SOC teams receive 4,484 alerts daily and spend nearly three hours a day manually triaging security alerts. That puts cybersecurity SOC analysts in a tough position. They’re the first in line to stop active threats, and they have to know what’s going on in their networks at all times. The problem is that SOC analysts deal with too many alerts to triage them all effectively.
55% of security teams say critical alerts are being missed, which fuels work frustrations for SOC analysts. It’s no wonder then that 62% of security professionals say that alert fatigue has led to staff turnove
- Too Many False Positives
43% of security pros find that 40% of their alerts are false positives.
SOC analysts deal with too many false positive security alerts. It’s tedious to sift through all the noise and find the real threats, which means SOCs are missing out on critical opportunities to stop threats early. This results in increased SOC analyst burnout and makes it harder for them to do their job effectively.
- Understaffed Security Teams
57% of the industry describes the global cybersecurity skills shortage as either ‘very bad ‘or ‘serious’.
Analysts are feeling the effects of understaffed security teams. They are often stretched thin, with little time for training or other SOC responsibilities. It also means that it takes longer for them to respond when incidents occur since there’s typically a backlog of work. SOC analysts must then take more time to investigate whether it’s a legitimate threat or false alarm — leading to wasted time and money spent investigating non-events.
- Poor Visibility in Environments
SOC analysts are tasked with addressing threats and vulnerabilities, but they don’t always have access to the data they need. Siloed tools and delayed data ingestion make it nearly impossible to get real-time data. Delays or incomplete analysis can lead to undetected threats.
It takes an average of 280 days to contain a data breach, which puts even more stress on analysts.
- Spending Too Much Time on Manual Tasks
78% of analysts say that it takes them an average of 10+ minutes to investigate each alert.
The amount of data that is collected in an enterprise environment is enormous, so it’s no surprise that SOC analysts spend most of their time collecting, analyzing and reporting on data. This leaves little time to triage critical alerts, proactively hunt threats, or invest in training. No wonder then that 92% of security professionals agree that automation is necessary to deal with these large alert volumes.
- Compliance Challenges
69% of security teams note that regulatory compliance is a major part of their security spending.
Compliance is a big deal for SOCs. It’s not just about keeping your organization out of hot water; it’s also about demonstrating to customers that you’re taking security seriously. But one of the biggest challenges faced by SOC analysts is maintaining compliance while working within constrained systems and budgets.
- Limited Security Budgets
Even amid expensive, damaging cyber-attacks, security teams still struggle with limited budgets. SOC analysts understand that there are solutions available to improve security performance, like dwell time, MTTD and MTTR. But if the budget isn’t there, analysts are stuck manually triaging threats.
Security teams need to be able to track security metrics and pull reports to demonstrate value. However, there usually isn’t enough time or enough existing capabilities to do this effectively.
SOC analysts are up against a deep sea of alerts. Considering the size and scope of any SOC, security analysts often have their hands full with large volumes of data and alerts to sift through.
SEE: What Coding Language Should I Learn for Cyber Security?
GRC vs SOC in 2025 and Beyond
The demand for both GRC and SOC Analysts is expected to soar as organizations continue to face regulatory changes and cybersecurity threats. According to CyberSeek, the cybersecurity job market in the U.S. alone has over 750,000 open roles, with SOC and GRC positions ranking among the most sought-after.
Key Trends to Watch:
- GRC Analysts: Increased focus on Environmental, Social, and Governance (ESG) compliance will drive demand.
- SOC Analysts: Rising adoption of AI and automation in threat detection will redefine the role but not diminish its importance.
Conclusion
As the cybersecurity landscape continues to evolve, the roles of GRC Analysts and SOC Analysts remain critical in safeguarding organizations against emerging threats and regulatory challenges. While GRC Analysts focus on governance, risk management, and compliance, SOC Analysts concentrate on real-time security monitoring and incident response.
Both roles offer lucrative career opportunities, competitive salaries, and paths for professional growth. As organizations increasingly recognize the importance of robust cybersecurity measures, the demand for skilled professionals in both areas is expected to rise.
In choosing between a career as a GRC Analyst or a SOC Analyst, individuals should consider their interests, skills, and career goals. Whether you are drawn to the strategic aspects of governance and compliance or the dynamic world of incident response and threat detection, both paths offer exciting opportunities to make a significant impact in the ever-evolving field of cybersecurity.
By understanding the nuances of each role, aspiring professionals can make informed decisions that align with their career aspirations and contribute to building a more secure digital future.
Transform your career with ExcelMindCyber’s roadmap to six-figure success in cybersecurity. Our program delivers essential guidance and strategies to help you master the skills and secure the roles that matter. Start today and take the first step towards transforming your career!
