
How to Start a Cybersecurity Firm
To understand how to start a cybersecurity firm, one must have it at the back of one’s mind that the cybersecurity industry has emerged as a critical pillar of global security infrastructure.
With the exponential increase in digital data, the reliance on technology in both personal and professional spheres has skyrocketed, making cybersecurity more relevant than ever. Once a niche IT concern, this field has become a paramount strategic imperative for organizations and governments worldwide.
The surge in cyber threats, ranging from data breaches and ransomware to sophisticated state-sponsored attacks, has escalated the demand for robust cybersecurity solutions. Cybersecurity Ventures predicts that global spending on cybersecurity products and services will exceed $1 trillion cumulatively over the five years from 2017 to 2021.
This growth is fueled by the need to protect proliferating digital assets, comply with regulatory requirements, and safeguard against increasingly advanced threats.
This article aims to provide a comprehensive guide for entrepreneurs and professionals interested in capitalising on this demand by starting a cybersecurity firm.
READ ALSO: The Future of Cybersecurity in the Age of AI (Artificial Intelligence)
The article covers all essential aspects, from understanding the dynamic landscape of cybersecurity to navigating the complexities of setting up and running a successful business in this domain. It seeks to inform, guide, and inspire those looking to make their mark in the cybersecurity world, providing actionable insights and practical advice on every step of the entrepreneurial journey in this field.
This introduction sets the stage for a detailed exploration into the exciting and challenging world of starting a cybersecurity firm, highlighting the industry’s significance and the opportunities it presents.

How to Start a Cybersecurity Firm: Current Trends
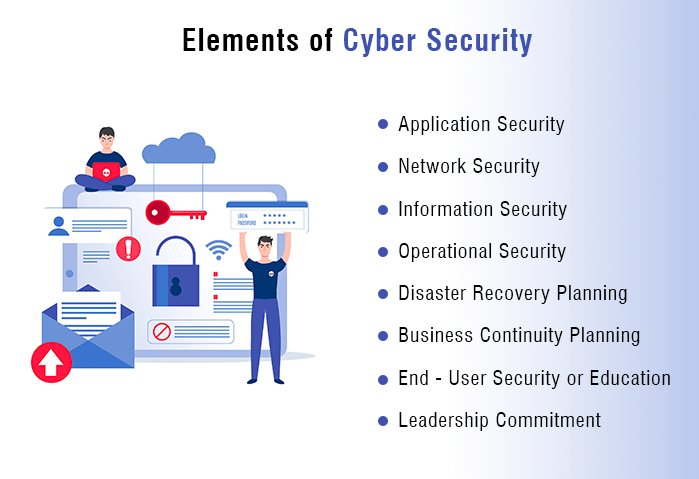
How to Start a Cybersecurity Firm
1. Increasing Sophistication of Cyber Attacks:
Cybercriminals are employing more sophisticated methods, including advanced persistent threats (APTs) and state-sponsored attacks, requiring equally advanced defence mechanisms.2. Rise of IoT and Mobile Vulnerabilities:
With the proliferation of IoT devices and mobile computing, new vulnerabilities have emerged, expanding the attack surface that cybersecurity firms must protect.3. Growing Importance of AI and Machine Learning:
Artificial intelligence (AI) and machine learning are increasingly used in cybersecurity for threat detection and response, making understanding these technologies crucial for new firms.4. Shift to Cloud Security:
As businesses move to cloud computing, the demand for cloud security solutions has escalated, focusing on protecting data and applications hosted in the cloud.5. Regulatory Compliance:
Stricter regulatory environments like GDPR in Europe have heightened the need for compliance, making cybersecurity not just a technical issue but also a legal one.Key Areas of Focus
- Corporate Cybersecurity: Protecting corporate networks, data, and assets from cyber threats. This includes securing enterprise IT infrastructure, managing access controls, and implementing cybersecurity policies.
- Government Cybersecurity: Assisting government entities in defending national infrastructure and sensitive data against cyber espionage and attacks.
- Personal Cybersecurity: Safeguarding individuals’ personal data, including identity protection, securing personal devices, and awareness training.
The Role of Emerging Technologies
- AI and Machine Learning: Utilizing AI for predictive threat analysis, anomaly detection, and automated incident response.
- Blockchain: Leveraging blockchain for enhancing data integrity and secure transactions, particularly in sectors like finance and supply chain.
- Internet of Things (IoT): Developing security solutions for the vast array of connected devices, addressing unique challenges in IoT security.
How to Start a Cybersecurity Firm: Technical Expertise Required
Technical expertise is paramount, encompassing areas such as network security, ethical hacking, incident response, data encryption, and cloud security. These skills are critical for protecting against intrusions, managing breaches, and ensuring data and cloud environments are secure. 1. Network Security: Proficiency in securing networks against intrusions, monitoring network traffic for suspicious activity, and implementing firewalls and intrusion detection systems. 2. Ethical Hacking: Skills in penetration testing and vulnerability assessments to identify and rectify security flaws before malicious actors exploit them. 3. Incident Response and Management: Ability to respond to and manage security breaches, including the capability to conduct forensic analysis and mitigate damage. 4. Data Security and Encryption: Knowledge of methods to protect data at rest and in transit, including encryption techniques and key management practices. 5. Cloud Security: Expertise in securing cloud environments, understanding cloud-specific vulnerabilities, and implementing best practices for cloud security.Importance of Continuous Learning and Certifications
In cybersecurity, the importance of continuous learning and certifications lies in keeping pace with evolving threats and technologies, and certifications like CISSP and CEH boost credibility. Similarly, understanding legal and regulatory frameworks is vital, requiring knowledge of compliance standards and skills in drafting legally sound contracts and policies. Staying Updated: Cybersecurity keeps developing rapidly, making continuous learning essential to stay abreast of the latest threats and technologies. Certifications: Obtaining industry-recognized certifications (e.g., CISSP, CISM, CEH) enhances credibility and demonstrates expertise to clients.Understanding Legal and Regulatory Frameworks
Compliance Knowledge: Familiarity with legal standards and regulatory requirements (like GDPR and HIPAA) is crucial for providing compliant cybersecurity solutions. Contract and Policy Drafting: Skills in drafting contracts, SLAs, and cybersecurity policies that meet legal standards and protect both the firm and its clients.How to Start a Cybersecurity Firm: Developing a Business Plan
 When developing a business plan in cybersecurity, key steps include conducting market research to identify underserved areas, specializing in niches like network or IoT security, and clearly defining your target audience, be it small businesses, large corporations, or specific sectors like healthcare.
When developing a business plan in cybersecurity, key steps include conducting market research to identify underserved areas, specializing in niches like network or IoT security, and clearly defining your target audience, be it small businesses, large corporations, or specific sectors like healthcare.
Identifying Your Niche and Target Market
1. Market Research: Conduct thorough research to identify gaps in the market. Focus on industries or sectors that are underserved or facing unique cybersecurity challenges. 2. Specialization: Consider specializing in a specific area of cybersecurity, like network security, IoT security, or cloud security, to differentiate your firm. 3. Target Audience: Define your target audience – whether it’s small businesses, large corporations, government entities, or specific industries like healthcare or finance.Assessing Competition and Market Needs
1. Competitive Analysis: Analyze your competitors to understand their offerings, strengths, and weaknesses. This can help in positioning your firm uniquely in the market. 2. Understanding Client Needs: Engage with potential clients to understand their specific cybersecurity concerns and requirements. Tailor your services to address these needs effectively. 3. Financial Planning: Budgeting, Pricing Strategies, and Funding Options 4. Budgeting: Develop a detailed budget that covers startup costs, operational expenses, marketing, salaries, and technology investments. 5. Pricing Strategies: Establish pricing models that are competitive yet profitable. Consider various models like subscription-based, per-project, or retainer agreements. 6. Funding Options: Explore different funding options such as bootstrapping, angel investors, venture capital, or small business loans. Choose the one that aligns best with your business goals and financial situation. A well-thought-out business plan is crucial for the success of a cybersecurity firm. It should clearly define the niche, understand the market and competition, and have a solid financial strategy. This foundation not only guides the firm through its initial stages but also helps in attracting investors and clients. RELATED: The Impact of Quantum Computing on CybersecurityLegal Considerations and Compliance
In establishing a cybersecurity firm, legal considerations and compliance are crucial. This involves registering your business with the appropriate authorities, a process that varies by region and may require specific licenses. Additionally, selecting the right business structure, such as a sole proprietorship, LLC, or corporation, is important for managing liability, taxes, and operational flexibility.Registering Your Business and Choosing a Business Structure
- Business Registration: Ensure legal compliance by registering your business with relevant authorities. This process varies by region and can include obtaining necessary licenses and permits.
- Business Structure: Choose an appropriate business structure (e.g., sole proprietorship, LLC, corporation) considering factors like liability, taxes, and operational flexibility.
Understanding and Adhering to Cybersecurity Laws and Regulations
Navigating cybersecurity laws and regulations is essential for any cybersecurity business. This includes staying informed about and complying with relevant laws like GDPR and HIPAA, and implementing robust policies to protect client data, adhering to strict privacy and data protection regulations. Regulatory Compliance: Stay informed about cybersecurity laws and regulations that affect your business and your clients, such as GDPR, HIPAA, or industry-specific regulations. Client Data Protection: Implement policies and procedures to ensure the protection of client data, complying with privacy laws and data protection regulations.Importance of Cybersecurity Insurance
Risk Management: Cybersecurity insurance is a critical component of risk management. It can protect your business from the financial consequences of data breaches, cyberattacks, and other security incidents. Client Assurance: Offering services backed by cybersecurity insurance can provide additional assurance to clients, showing that your firm is prepared for potential risks. Legal considerations and compliance are integral to establishing and operating a cybersecurity firm. Proper legal setup, adherence to regulations, and obtaining cybersecurity insurance not only protect the firm but also build trust with clients. It’s essential to navigate these aspects carefully, possibly with the assistance of legal professionals specializing in cybersecurity and business law.How to Start a Cybersecurity Firm: Building Your Team
Building a strong team is key in cybersecurity. Focus on hiring professionals with robust technical expertise in areas like network or cloud security and value certifications like CISSP or CEH as markers of proficiency. Equally important are problem-solving abilities, as cybersecurity challenges require sharp analytical and critical thinking skills.Qualifications and Experience to Look For
- Technical Expertise: Look for candidates with strong technical skills in areas relevant to your services, such as network security, encryption, or cloud security.
- Certifications: Consider certifications like CISSP, CISM, or CEH as indicators of a candidate’s knowledge and commitment to the field.
- Problem-Solving Abilities: Cybersecurity is about solving complex problems. Candidates should demonstrate strong analytical and critical thinking skills.
Creating a Culture of Security and Ethical Practices
Security-First Mindset: Instill a culture where security is a top priority. Regular training and awareness programs can keep the team updated on the latest threats and best practices. Ethical Standards: Uphold high ethical standards. This includes responsible handling of sensitive information and adhering to professional codes of conduct.The Role of Training and Professional Development
Continuous Learning: Encourage continuous learning and professional development among your team members. This could be through workshops, courses, or attending industry conferences. Internal Training Programs: Develop internal training programs to keep your team skilled in the latest cybersecurity technologies and practices. Building a competent and reliable team is crucial for the success of a cybersecurity firm. The team should possess the necessary technical skills and align with the firm’s ethical standards and culture of security. Investing in your team’s continuous learning and professional development is vital for staying ahead in the field of cybersecurity.Technology and Infrastructure
The foundation of a cybersecurity firm is its technology and infrastructure. Selecting the right tools and technologies is not just about having the latest gadgets; it’s about choosing solutions that align with your firm’s services and client needs. This includes everything from advanced security software to robust hardware and network systems. Your technology stack should be scalable, allowing for growth and adaptation as your firm evolves and as new threats emerge. Setting up a secure and efficient operational infrastructure is equally critical. This goes beyond physical hardware; it involves creating a network that’s not only resilient against attacks but also optimized for performance. Cybersecurity firms must practice what they preach, ensuring their own systems exemplify the highest standards of security. This includes regular updates, patches, and adherence to best practices in IT security. The role of cloud services and data centres in today’s cybersecurity landscape cannot be overstated. These solutions offer flexibility, scalability, and cost-efficiency. However, they also come with unique security challenges. A cybersecurity firm must be adept at navigating these challenges, offering cloud-based solutions to clients while maintaining impeccable security standards. In essence, the technology and infrastructure of a cybersecurity firm are its backbone. These elements must be carefully planned and continuously managed to ensure the firm can reliably protect itself and its clients from cybersecurity threats.Marketing and Client Acquisition
Branding and Positioning Your Firm in the Market
Developing a strong brand identity is crucial for a cybersecurity firm. This involves creating a compelling brand message that resonates with your target audience and differentiates your firm from competitors. Your branding should reflect your firm’s expertise, values, and unique selling proposition. Consider the visual aspects (like logos and colour schemes) and the messaging (such as your mission statement and marketing materials).Digital Marketing Strategies
- Search Engine Optimization (SEO): Optimize your website and content to rank higher in search engine results, making it easier for potential clients to find you.
- Social Media Marketing: Utilize platforms like LinkedIn, Twitter, and Facebook to engage with your audience, share industry insights, and promote your services.
- Content Marketing: Publish informative blogs, whitepapers, and case studies that showcase your expertise and provide value to your audience.
- Email Marketing: Use email campaigns to nurture leads, keep clients informed about your services, and share industry news and updates.
Building Client Relationships and Networking
Networking is a powerful tool for client acquisition in the cybersecurity industry. Attend industry conferences, seminars, and webinars to connect with potential clients and partners. Building strong relationships with other businesses can lead to referrals and collaborative opportunities. Additionally, consider joining professional associations and online forums to expand your network. Leveraging both digital marketing strategies and traditional networking can significantly enhance your firm’s visibility and attract potential clients. Effective marketing requires a balanced approach, combining online presence with personal connections, to establish trust and credibility in the cybersecurity market.Managing Cybersecurity Risks in Your Firm
 Cybersecurity firms, while providing security services, are not immune to the very risks they protect against. It’s crucial to implement robust internal cybersecurity protocols. This involves regularly updating and patching systems, employing advanced threat detection and response tools, and conducting periodic security audits. These practices not only safeguard the firm’s data and assets but also serve as a testament to its commitment to security, reinforcing client trust.
Regular audits and compliance checks are essential. These should be comprehensive, covering all aspects of your business operations, from employee access controls to data handling and client communication. These audits help in identifying potential vulnerabilities and ensuring that the firm adheres to industry best practices and regulatory requirements.
Staying updated with the latest cybersecurity threats and solutions is vital. This means keeping abreast of emerging threats, evolving attack vectors, and new mitigation strategies. It also involves investing in ongoing education and training for your team to ensure they are equipped with the latest knowledge and skills.
Effective risk management in a cybersecurity firm is about leading by example. By maintaining stringent security practices internally, the firm not only protects itself but also demonstrates to clients its expertise and commitment to cybersecurity. This proactive approach to managing risks is integral to building and maintaining a reputation as a reliable and trusted cybersecurity provider.
MORE: Cybersecurity Salary: A Comprehensive Guide
Cybersecurity firms, while providing security services, are not immune to the very risks they protect against. It’s crucial to implement robust internal cybersecurity protocols. This involves regularly updating and patching systems, employing advanced threat detection and response tools, and conducting periodic security audits. These practices not only safeguard the firm’s data and assets but also serve as a testament to its commitment to security, reinforcing client trust.
Regular audits and compliance checks are essential. These should be comprehensive, covering all aspects of your business operations, from employee access controls to data handling and client communication. These audits help in identifying potential vulnerabilities and ensuring that the firm adheres to industry best practices and regulatory requirements.
Staying updated with the latest cybersecurity threats and solutions is vital. This means keeping abreast of emerging threats, evolving attack vectors, and new mitigation strategies. It also involves investing in ongoing education and training for your team to ensure they are equipped with the latest knowledge and skills.
Effective risk management in a cybersecurity firm is about leading by example. By maintaining stringent security practices internally, the firm not only protects itself but also demonstrates to clients its expertise and commitment to cybersecurity. This proactive approach to managing risks is integral to building and maintaining a reputation as a reliable and trusted cybersecurity provider.
MORE: Cybersecurity Salary: A Comprehensive Guide
Future of Cybersecurity and Scaling Your Business
Technological advancements continuously shape the cybersecurity industry. To remain relevant and competitive, your firm must stay abreast of emerging technologies like artificial intelligence (AI), blockchain, and quantum computing. These technologies not only bring new tools to enhance your cybersecurity offerings but also introduce novel challenges and threats that your firm should be prepared to address.Expanding Services and Scaling Your Business
- Diversification: Consider expanding your service offerings to include newer areas of cybersecurity, such as IoT security, cloud security, or cybersecurity training services.
- Geographical Expansion: Look for opportunities to serve clients in different regions or countries, which can diversify your client base and reduce market-specific risks.
- Strategic Partnerships: Forming partnerships with other firms or vendors can provide access to new markets, technologies, and expertise, aiding in business growth.
- Talent Acquisition: As you scale, hiring additional skilled professionals and potential specialists in new areas of cybersecurity is essential to support the expanded workload and expertise required.
How to Start a Cybersecurity Firm: Long-term Strategies for Success
For long-term success in cybersecurity, it’s crucial to cultivate a culture of continuous learning and innovation, constantly updating skills and knowledge to stay ahead of industry trends. Adopt a client-centric approach, focusing on delivering exceptional, tailored solutions that meet evolving needs. Be flexible in adapting business strategies based on industry shifts, client feedback, and performance metrics. Staying agile and responsive to change, scaling services effectively, and maintaining a strong client focus are key to thriving in the dynamic field of cybersecurity.- Continuous Learning Culture: Foster a culture of continuous learning and innovation within your firm. Encourage your team to pursue ongoing education and stay informed about the latest industry trends and techniques.
- Client-Centric Approach: Maintain a focus on delivering exceptional value to your clients. This includes not just technical excellence but also understanding their evolving needs and providing tailored proactive solutions.
- Adaptive Business Strategies: Be prepared to adapt your business strategies in response to industry changes, client feedback, and internal performance metrics.
Conclusion
In embarking on the journey of how to start a cybersecurity firm, entrepreneurs face a landscape filled with challenges but also abundant with opportunities. By staying informed, adaptable, and client-focused, and by building a strong foundation in both technology and business acumen, one can navigate this dynamic field towards a successful and impactful cybersecurity venture. This endeavour not only promises business success but also contributes significantly to the broader goal of creating a safer digital world.FAQ
What are the initial costs involved in starting a cybersecurity firm? The initial costs can vary widely but generally include expenses for legal setup, technology and software, office space (if required), marketing, and staff salaries. Investment in cybersecurity-specific tools and infrastructure is also a significant part of the startup cost. How long does it take to establish a cybersecurity firm? The timeline can vary based on numerous factors, including business planning, acquiring clients, setting up operations, and market conditions. Generally, it might take several months to a year to get the business operational. What are the biggest challenges in starting and running a cybersecurity firm? Key challenges include staying updated with rapidly evolving cyber threats, hiring skilled professionals, continuous technological upgrades, and maintaining a steady client base in a competitive market. How important is having a niche in cybersecurity? Specializing in a niche can help differentiate your firm in a crowded market. It allows you to focus on specific client needs and build deep expertise, although it’s also important to balance specialization with the flexibility to adapt to market changes. What strategies are most effective for client acquisition? A combination of digital marketing, networking, and referrals tends to be effective. Building a strong online presence, attending industry events, and leveraging satisfied clients for referrals can significantly aid in acquiring new clients. Is it necessary to have a physical office space for a cybersecurity firm? It’s not always necessary, especially in the initial stages. Many cybersecurity services can be provided remotely. However, having a physical office can add credibility and might be preferred by some clients. Transform your career with ExcelMindCyber’s roadmap to six-figure success in cybersecurity. Our program delivers essential guidance and strategies to help you master the skills and secure the roles that matter. Start today and take the first step towards transforming your career!
