
The Impact of Quantum Computing on Cybersecurity
If there was a world where the rules of quantum mechanics empower us to tackle complex problems that once lay beyond the grasp of classical computers. Quantum computing takes us on this remarkable journey.
With the ability to process colossal volumes of data and perform simultaneous computations at extraordinary speeds, quantum computers have the potential to redefine entire fields like medical research, artificial intelligence, and weather forecasting. Yet, there’s another side to this technological marvel—a side that raises significant concerns about cybersecurity.
This article will explore the intricate landscape where quantum computing meets cybersecurity, revealing both the promising horizons and the lurking shadows. It’ll also explain the steps we can take to prepare for a quantum-secure future.
READ ALSO: The Future of Cybersecurity in the Age of AI (Artificial Intelligence)
How Quantum Computing Could Break Encryption
At the heart of modern cybersecurity lies encryption – a process that transforms data into an enigmatic code, decipherable only by those with the right key. It’s the silent guardian of our online transactions, communications, and the sanctity of our data.
Consider the moments when you make an online purchase or access your work emails remotely – encryption is your trusty shield, safeguarding personal and financial information from the prying eyes of hackers and eavesdroppers.
But here’s the catch: encryption is not an impenetrable fortress. It relies on intricate mathematical puzzles that challenge classical computers, though they are not entirely invincible.
One of the prevailing encryption methods relies on a curious principle – multiplying two large prime numbers is a breeze, but unraveling their product is an exceptionally tough nut to crack. Enter the RSA algorithm, a stalwart in the encryption world.
While a classical computer might toil for millions of years in a futile attempt to breach a 2048-bit RSA key, a quantum computer could make short work of it in mere minutes or hours, all thanks to Shor’s algorithm.
There’s more to this quantum arsenal, including Grover’s algorithm, which could dismantle other encryption methods like elliptic curve cryptography (ECC) and symmetric-key cryptography (SKC).
This disconcerting revelation implies that quantum computers have the potential to unlock any data protected by today’s standards, laying bare sensitive information ranging from passwords, credit card numbers, and health records to closely guarded trade secrets and even national security data.
In this fascinating yet perilous interplay of quantum computing and encryption, we tread the line between immense promise and undeniable threats. It is this duality that beckons us to prepare for a future where the quantum realm, both friend and foe, is navigated with utmost caution.
How Quantum Computing Could Improve Encryption
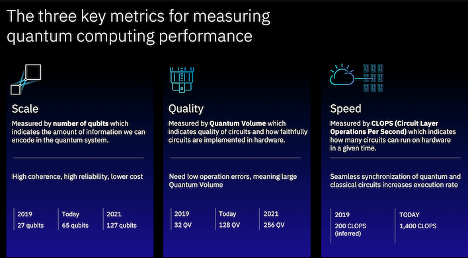
Quantum Computing Speed Metric | Photo Credit: Fierce Electronics
Quantum computing serves as a catalyst for the development of robust encryption algorithms and security protocols designed to withstand quantum attacks. Among the stars in this realm, we find quantum key distribution (QKD).
QKD is akin to a celestial dance of quantum particles, chiefly photons or electrons. These particles exhibit a mesmerizing property—superposition, where they can exist in multiple states simultaneously, only collapsing into a definite state when measured.
What’s truly remarkable is that any attempt to observe or meddle with these particles results in an immediate change in their state, alerting us to the presence of an intruder. This inherent characteristic renders QKD impervious to eavesdropping and tampering.
The promise of QKD extends its reach to securing quantum communications through satellites and expansive optical fiber networks. Moreover, it has the versatility to integrate seamlessly with classical encryption techniques, forming hybrid systems that embody both speed and security.
Though QKD has seen the light in various experiments and applications across the globe, there are still hurdles and limitations to surmount before it can take its place on the grand stage of accessibility.
SEE ALSO: Home Wi-Fi Network: A Complete Guide
How to Prepare for a Quantum-safe Future
Experts in the field suggest that it will take at least another decade before we see quantum computers boasting a substantial number of qubits. However, let’s not be lulled into complacency.
Today’s encrypted data may be a treasure trove for adversaries, awaiting decryption once quantum computers attain sufficient might. This scenario is known as the “harvest-and-decrypt” attack, emphasizing the urgency to prepare for a quantum-safe future without delay.
One proactive stride we can take is the adoption of post-quantum cryptography (PQC). PQC ushers in a new era of classical cryptographic algorithms engineered to fend off quantum threats.
These algorithms grapple with mathematical problems challenging to both classical and quantum computers, including lattice-based cryptography, code-based cryptography, multivariate cryptography, hash-based cryptography, and supersingular isogeny cryptography.
As we tread this path, it’s important to note that PQC standards are still in the making, led by organizations such as the National Institute of Standards and Technology (NIST) in the US and the European Telecommunications Standards Institute (ETSI) in Europe.
Nevertheless, several PQC algorithms have already undergone implementation and testing by various entities. Google, for example, has ventured into the realm of PQC with an algorithm named NewHope in its Chrome browser, while Microsoft has introduced a PQC library known as Microsoft SEAL.
Beyond adopting resilient encryption, awareness is key. Understanding the dynamics of quantum computing, its implications for cybersecurity, and how to mitigate risks is a shared responsibility.
Collaboration is the cornerstone, uniting governments, industry, academia, and civil society to craft and implement quantum-safe policies and practices. Quantum computing has irrevocably changed the landscape of cybersecurity. Our response must be poised and collective to shape a quantum-safe future, transforming a potential threat into a remarkable opportunity.
Conclusion
Quantum computing emerges as a transformative force, harboring the power to reshape countless domains. Yet, it wields a double-edged sword, threatening the sanctuary of our data and communications. To guard against this potential peril, we must embrace quantum-resistant encryption technologies, such as quantum key distribution and post-quantum cryptography.
Moreover, we must educate ourselves and others about the profound implications of quantum computing for cybersecurity and collaborate to build a quantum-safe future. Quantum computing isn’t a foe to be ignored but an ally to be harnessed.
FAQ
What is Quantum Computing, and How Does It Affect Cybersecurity?
Quantum computing harnesses the principles of quantum mechanics to process vast amounts of data at unprecedented speeds. This ability poses significant challenges to traditional encryption methods, raising concerns about the security of current cybersecurity measures.
Can Quantum Computers Break Current Encryption Standards?
Quantum computers have the potential to break widely used encryption standards like RSA and ECC. Algorithms like Shor’s algorithm can solve mathematical problems much faster than classical computers, threatening the integrity of current encryption methods.
What is Quantum Key Distribution (QKD) and How Does It Improve Encryption?
Quantum Key Distribution is a method of secure communication that uses quantum mechanics properties. It ensures security by alerting parties to any eavesdropping attempts, making it a promising solution for quantum-proof encryption.
What is Post-Quantum Cryptography, and Why is it Important?
Post-quantum cryptography refers to cryptographic algorithms that are secure against both quantum and classical computers. As quantum computing advances, PQC becomes essential to protect sensitive data from potential quantum computing threats.
How Can We Prepare for a Quantum-Safe Future?
Preparing for a quantum-safe future involves adopting quantum-resistant encryption technologies like QKD and PQC. It also requires collaboration among governments, industries, and academia to develop and implement effective quantum-safe strategies and policies.
